
29 October 2015 / JC's Column / JC Gaillard
In earlier articles this year, we examined the challenges the CIO faces around Information Security, the importance of the CISO’s reporting line, and the fundamental role the Board of Directors has to play to drive security transformation. In part 2 of… Read more »

22 October 2015 / JC's Column / JC Gaillard
In earlier articles this year, we examined the challenges the CIO faces around Information Security, the importance of the CISO’s reporting line, and the fundamental role the Board of Directors has to play to drive security transformation. In this shor… Read more »

20 October 2015 / Company Information / Neil Cordell
Technology alone will not protect you from Cyber Threats It was a great pleasure for Corix Partners to be invited to present at the Central London and North Thames area regional meeting of the Chartered Institute of Management Accountants (CIMA) on Thu… Read more »

15 October 2015 / Neil's Column / Neil Cordell
First focus on the business challenge Before you even look at the available technology solutions, the first step to success is to consider the business challenge that you are trying to solve. Matters for consideration include: who in the organisation s… Read more »

8 October 2015 / Guest Blog / Rick Warley
We are all faced with risks every day; with decisions that can have potentially catastrophic consequences. Assessing risk is something we have been coached to do on a daily basis from a young age: Is this wall too high to jump off? Can I cross the road… Read more »

1 October 2015 / Architecture and Design / Neil Cordell
Why are so many technology solutions not secure? Many IT projects encounter serious issues when they run into delays too close to the implementation “go live” date because they are considered to be “not secure enough”. It seems incredible that the situ… Read more »

24 September 2015 / Leadership Development / Corix Partners
In this article we explore the profile of the CIO – providing advice to junior IT professionals wishing to develop into the role. As well as discussing the CIO’s roles and responsibilities, we also highlight the key qualities recruiters look for – and… Read more »

17 September 2015 / Neil's Column / Neil Cordell
One of the common problems in Information Security is the belief that a technology solution will be able to resolve all the security problems that an organisation faces. As a consequence, Information Security professionals have the tendency to dive str… Read more »
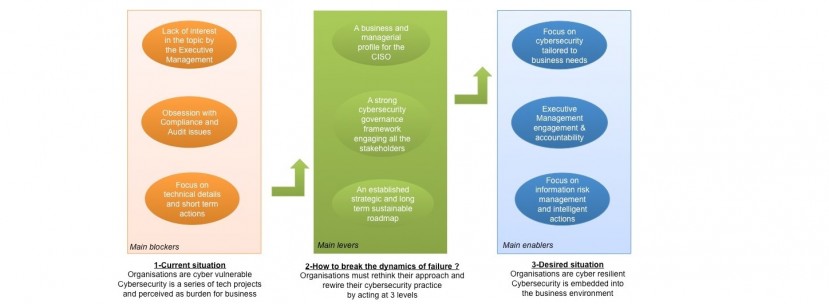
10 September 2015 / Strategy and Governance / JC Gaillard
The current cyber security situation in many large organisations is dominated by significant blockers. Cybersecurity is still broadly perceived as an IT discipline, built around technical solutions and projects – you only have to open any industry maga… Read more »

3 September 2015 / Leadership Development, Strategy and Governance / JC Gaillard
This article is a summary of the series “The CIO Guide to a successful Information Security Practice – 8 Key Management pitfalls to avoid” published on our blog in May and June 2015. The series deconstructs eight commonly held views on Information Secu… Read more »

