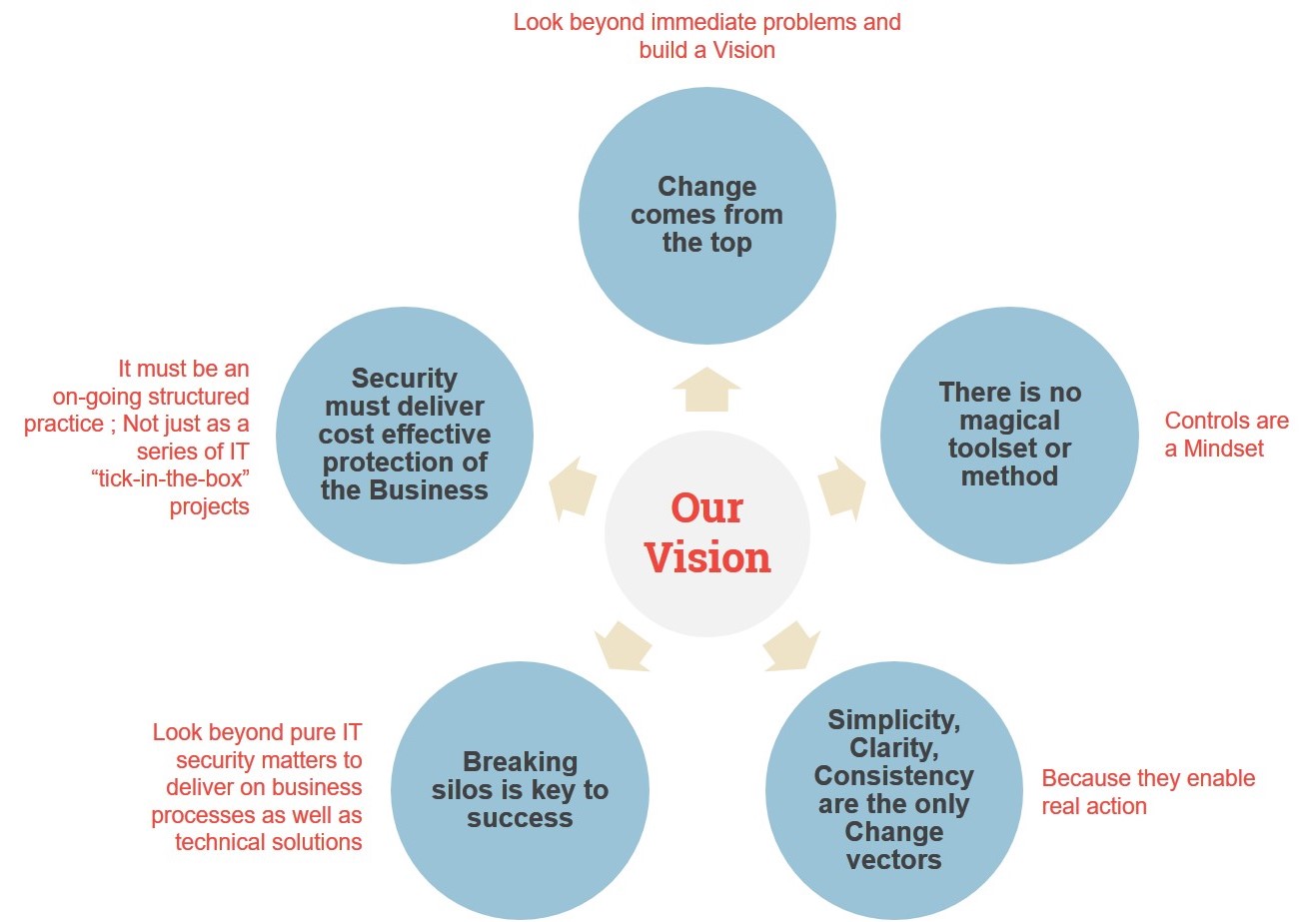
Organisational Change come from the top
Look beyond immediate problems and build a Security Vision
Work from the top and build a mid to-long term Business Protection Vision
- Immediate problems and tactical point solutions needed? Address them but look beyond
- Create a sense of urgency, direction and purpose, and stick to it
- Break Silos ; Look at federating and structuring all aspects of the Enterprise Controls Framework
There is no magical tool or method
Controls are a Mindset
Governance and Culture are key
- From BCP, IT & Physical Security, to third-party management, Operational Risk, Compliance, Audit and Insurance practices
- Real Change in the Security Controls field is complex and takes time
- Security Controls are a Mindset, not a necessary evil or an occupational hazard
Simplicity, Clarity, Consistency
Are the only change vectors because they enable real action
Real Change is enacted at the bottom and comes from real action
- Keep plans simple and focus teams on clear objectives: Common sense goes a long way in the Controls field
- Adjust priorities or timeframes if needed but resist deviations whatever happens
Breaking silos is key to success
To deliver on business processes as well as technical solutions
Look beyond pure IT security matters
- Technical information security initiatives are often complex and cross-discipline which require a focus on IT and Security Governance
- Involve all stakeholders from the start and keep them involved through the production of meaningful and usable metrics
- Breaking silos across Security, IT and the Business to deliver real effective and efficient control platforms and ongoing support around those is key to success
Information Security as an on going structured practice
That delivers cost effective protection of the Business
Not just as a series of “tick-in-the-box” projects
- Establish a clear operating model across IT, Security, the Business, and other control functions (Risk, Compliance, Audit)
- Ensure security roles, responsibilities and reporting lines are clear and at the right level
- Establish true ownership and accountability for information security controls and business protection across the Enterprise
If you like our Vision and share our Values, click here to join our newsletter for more Cyber Security Leadership insights, or visit our blog

