To many organisations, Information Security is something which has historically been approached from an audit or compliance perspective. Questions such as “what do we need to do in order to correct these audit issues?” and “which boxes do we need to tick in order to satisfy regulators?” are unfortunately still quite common. Despite a significant evolution of cyber risk over the past ten years, many organisations still regard Information Security as a purely technical task or a policy writing exercise – rather than addressing issues across the organisation in order to build a robust and long-lasting strategic approach to security.
At Corix Partners, this concerning attitude towards InfoSec matters is something we have witnessed time and time again. Over the course of our many years working in the Information Security field, we have developed an approach to security which focuses on building durable long-term protection against Information Security threats. In order to be successful, Information Security cannot be seen merely as a collection of IT projects aimed at resolving audit or compliance issues. It must be treated as an ongoing practice and embraced as a mindset which is embedded into the daily operations of an organisation – across all levels of the business.
The importance of organising Information Security in a structured way
Information Security is also often approached in a reactive manner, in response to events such as data theft incidents or other types of cyber attacks. In order to see the value of properly addressing Information Security issues, it’s important to realise the real value of information within a business. Information is a highly valuable asset that is essential to the day-to-day operations of most businesses. It is targeted by a growing number of threats and needs to be protected like any other key asset. This is particularly true in industries such as the financial or retail sectors (online or not), where large volumes of highly confidential information are processed on a daily basis.
Information, electronic or not, is increasingly fragmented across various media and is no longer contained within the enterprise “hard shell”. In an increasingly connected workspace, organisations are becoming more and more vulnerable to external attacks. Information Security breaches are a very real and ongoing threat – and the full impact that attacks and breaches can and do have on organisations is becoming difficult to predict, with the potential to cause catastrophic brand damage and attract the attention of politicians and global media.
However, it’s not the security rules themselves which protect an organisation – it’s the real application of those controls in the field on a daily basis, across all staff members at every level which forms a strong shield in front of valuable information assets. It can only be driven efficiently and effectively through a structured organisation where roles, responsibilities and accountabilities are clearly defined – and supported by the right HR structures in terms of performance management and rewards.
Key challenges in organising Information Security
An effective Information Security Practice must provide a common controls framework clearly delineated across IT and the business for all parties to operate within.
When developing a robust Information Security Practice, it’s only natural that organisations will encounter challenges – as is often the case with any organisational change. It’s only through clarity, simplicity and consistency that the CISO will drive lasting change on these matters as they are the only true change vectors.
Before implementing an Information Security Practice, it is essential to identify the scope of its goals – ensuring they remain both simple to understand, at every level within the organisation, and truly achievable.
Information Security must have a simple and natural protective purpose. It cannot be seen as a complex technical matter reserved to experts. Its objectives should be immediate to all staff, without any need to raise “awareness” on these matters.
Then, momentum will often be required in order to drive change – getting multiple parties on the same page, working towards a common goal without causing unnecessary conflict or interference. This can be particularly challenging in larger, international firms with multiple workforces – each with their own unique business culture and used to operating in silos. The organisational model must allow the InfoSec practice to reach across these silos and influence across the business. It needs to encompass a governance model also designed to work in such a way.
Finally, it’s also vital to look beyond head-office and beyond the historical walls of the organisation. It is necessary to address the true geographical footprint of the business and issues like vendor risk when working with third parties – ensuring that relevant controls are in place internally, externally and across the world, in order to maintain a solid Information Security Practice that genuinely protects the business.
Building a successful Information Security Practice
In order to successfully develop and implement this, there are 3 key governance principles to consider:
- The reporting line of the CISO is the first key aspect, and must be determined in relation to the real profile of the role. The importance and the visibility of the CISO reporting line is absolutely paramount in our opinion – and it should be to the CIO or the COO in most cases. Delegating down, using multiple reporting lines or reporting lines to a committee will create ambiguity – damaging any change momentum – and must simply be avoided. Read more about the reporting line of the CISO in our April 2015 article.
- The personal profile of the CISO is also key. Only with the right level of management experience and personal gravitas can the CISO influence successfully across the real fabric of the business. In large organisations, this is one of the key challenges faced by most CIOs or COOs in that respect. Read more about The Key Governance Challenges of the CIO in our February 2015 article published on the theCsuite.co.uk.
- Finally, the Information Security Practice must be structured in a way that enables it to engage with all stakeholders. Defining a solid Information Security governance framework is key to success and must come first, together with a clear and simple security strategic roadmap. Read more about Information Security Governance in our February 2015 article.
Information Security can be structured and work as a matrix if these principles are respected. We offer a typical organisation chart (below) for a traditional “second line of defence” type of function to complement earlier postings (only to be seen as an example, as each organisation will have its own particular approach to naming or positioning controls functions and drawing such charts):
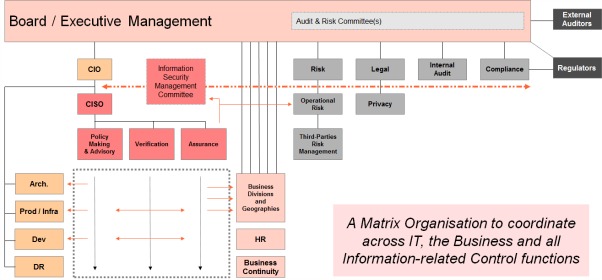
Corix Partners are experts at organising Information Security for success and driving real, lasting change in that space across large organisations.
Contact Corix Partners to find out more about developing a successful Information Security Practice for your business.
Managing Director – Corix Partners
www.corixpartners.com
Corix Partners is a Boutique Management Consultancy Firm, focused on assisting CIOs and COOs in resolving Security Strategy, Organisation & Governance challenges.

