Over recent years, the GRC (Governance, Risk and Compliance) acronym has become very common in the Information Security community. Various groups discuss the topic actively on professional social media, and countless software and service vendors appear to be offering solutions in that space. There seems to be a variety of views on the topic and a number of competing approaches or practices.
At face value, it is easy to see Information Security Governance, Risk Management and Compliance as three different disciplines. But it can also make a lot of sense to bundle them into one concept, leading to a sound implementation of Information Security in a “second line of defence” position – as long as the three aspects are architected in a coherent manner and their meaning is common to all stakeholders. They must form part of a structured Internal Controls Management Model, aimed at delivering an Internal Controls Strategy.
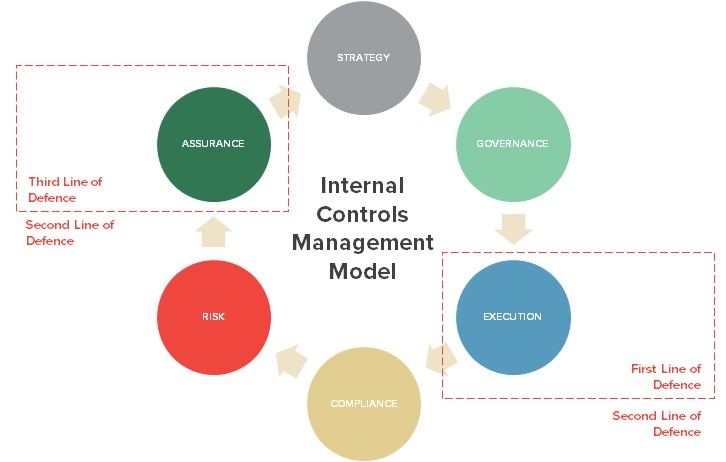
We have repeatedly commented in earlier articles on the paramount importance of a sound Governance Framework to drive a successful Information Security practice. At the heart of Security, you must have the need (shared by all stakeholders) to protect the business from the real and active Threats it faces – through the application of relevant and proportionate Controls. Good Governance is key to creating the dynamics that will ensure this happens.
We have also highlighted that Risk derives directly from the presence or absence of Controls to protect the business from real and active Threats, and can only be managed from the perspective of a sound Threats and Controls model.
There is no denying that Information Security Governance and Risk Management are key pillars to a successful Information Security practice, but Compliance can be a different matter altogether.
On its own, the term “Compliance” can mean different things to different people – and that’s where the problem truly starts. Quite often, it will be understood as meaning compliance with relevant regulatory obligations and applicable laws. While this may be the only driving force senior executives recognise in the Information Security field, it is too restrictive on its own to structure a sound Information Security practice around.
Organisations should primarily be concerned about ensuring compliance with their own internal policies, which should be there to drive adherence to a set of controls required to protect the business against real and active threats.
The Information Security aspects of regulatory and legal obligations should be built into those internal policies. These various elements overlap with established good practices in many ways but, in addition, there will be Controls that may not be contained explicitly in regulations or legislation that are nevertheless necessary for the good operations of the business.
CIOs and CISOs must treat Information Security Compliance as a by-product of the adherence to policies, standards and procedures set out to protect the business – and not as an objective by itself. Where Information Security is dissociated from the real need to protect the business against real threats, and is simply focused on regulatory or compliance matters, it tends to drift towards becoming a mere box-checking activity – or (at worst) a window-dressing exercise, at great cost and providing questionable value in all cases.
Once the right policy framework is established, an independent verification of policy Compliance is key to the production of meaningful and valuable Management Information – showing the levels of protection achieved across the organisation. This is the only way for Management to drive relevant actions in that space and make the right investment and budgetary decisions, amongst others.
However, these practices will only form the backbone of a wonderful ivory tower, if they are not rooted in the reality of proportionate Controls and the real and proper application of those Controls every day in the field by all stakeholders. Only properly implemented Controls can protect the business from the Threats it faces, not GRC alone.
A sound Information Security Governance Framework is paramount, and should lead to the definition of proportionate Controls to protect the business against the key threats it faces, and to their acceptance by all stakeholders (without complacency with regards to the true geographical footprint of the business or its dependence on third-parties).
In a traditional “three lines of defence” model, the Governance Framework should distribute roles and responsibilities to those stakeholders in a “first line of defence” for the application of those Controls in the field, and to the Information Security practice in a “second line of defence” for independent verification, risk management, reporting and escalation. The Information Security practice should also assist stakeholders in the understanding of the overall Controls Framework and, where necessary, guide them towards implementation – but under no circumstances should it cross the line and accept accountability for Controls delivery.
It is only on that basis that a meaningful Risk posture can be determined (based on the – independently verified – presence or absence of the mandated Controls), and lead to the production of meaningful Management Information (including regulatory Compliance Reporting where relevant). In turn, only accurate and meaningful Management Information can enable senior executives to understand the Risk situation the business faces, prioritise action and make the right decisions in that respect – including investment or budgetary decisions.
A sound Governance model, independent verification of policy Compliance, and a solid Risk Management and Reporting practice can form the backbone of a proper “second line of defence” implementation for Information Security – but it can only make sense in the context of a clear and meaningful operating model which also distributes “first line” responsibilities to stakeholders and ensures a common understanding of roles and concepts by all parties.
The diagram below offers an example of how these activities could be architected around a simplistic PDCA cycle.
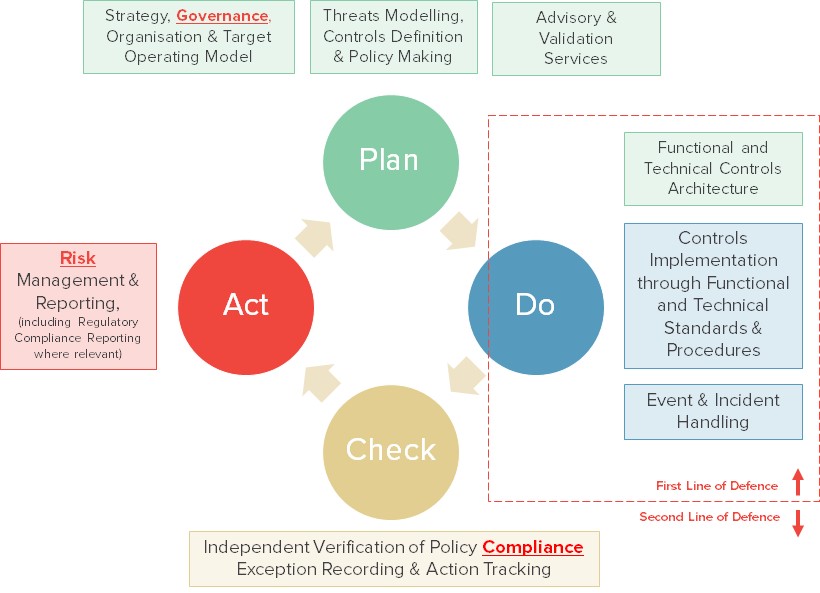
The key to make this work in real life lies at the interface between the first and second line of defence and in their day-to-day interaction. Demarcation lines must be clear and unambiguous, understood and accepted by all parties. The “second line” must not see itself as “running the show” and the “first line” must not see the “second line” as “interfering” or “looking over its shoulder”.
The Governance model should balance powers by granting the “first line” a validation role with regards to Threats, Controls and Policies – and a form of involvement in the definition and validation of resulting actions.
Both first and second lines of defence must work hand in hand to protect the business and internal politics must not be allowed to rule the game.
Managing Director
Corix Partners
Contact Corix Partners to find out more about developing a successful Information Security Practice for your business. Corix Partners is a Boutique Management Consultancy Firm, focused on assisting CIOs and COOs in resolving Security Strategy, Organisation & Governance challenges.

