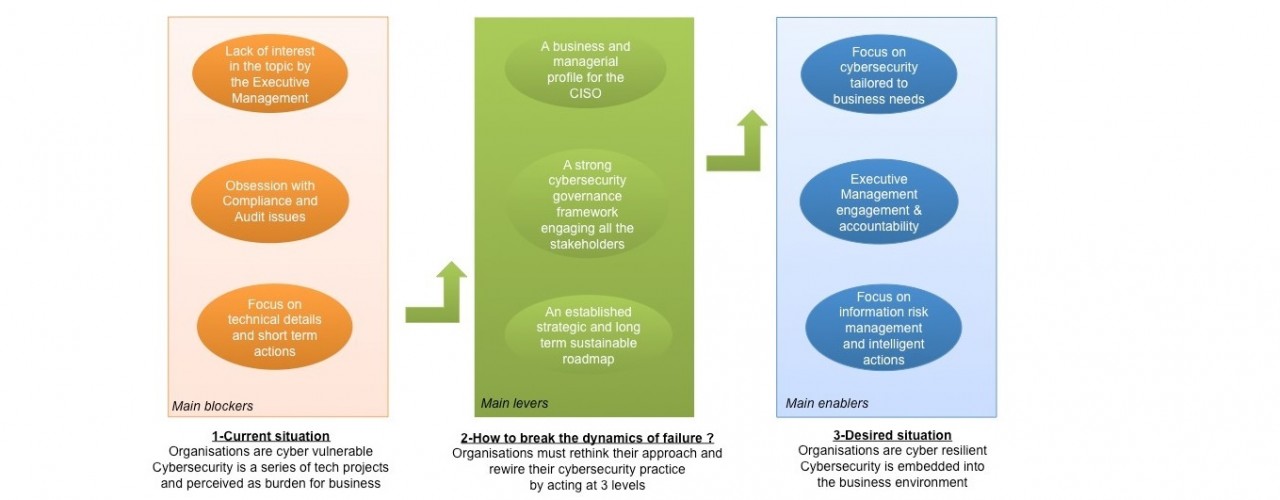
The current cyber security situation in many large organisations is dominated by significant blockers.
Cybersecurity is still broadly perceived as an IT discipline, built around technical solutions and projects – you only have to open any industry magazine or publication to see it, or go to any professional show.
The “three lines of defence” models promoted in some form or another by various standards, such as COSO or ISO 31000, are poorly understood and poorly applied. Cybersecurity is often arbitrarily kept in a technical first line, in spite of its complex nature, requiring a true implementation across the three lines of defence – and across many corporate silos.
In practice, this excessive technical focus – which spans the entire industry history – is failing for most large organisations. In fact, many of these organisations claim to spend in excess of 3% of their total IT spend on cybersecurity, but in spite of the amounts invested over the years – 79% have not yet achieved an acceptable level of cybersecurity maturity (‘Risk and Responsibility in a Hyper-connected World’ – World Economic Forum, January 2014). These results are echoed by the RSA Cyber Poverty Index published in June 2015.
This failing situation is rooted in the lack of cultural fit between cybersecurity and IT mindsets. Technologists are essentially trained and incentivised to deliver functionality and features – not risks and controls – and this leads to a tactical and technical security focus that rarely delivers true results in large organisations.
Those large organisations have become increasingly dependent on a larger and larger number of third parties, with cybersecurity problems often global and complex in nature, and the threats they face continue to evolve at a faster and faster pace. The geographical, operational and technical complexity of large organisations requires a well-designed strategy and proper governance framework, that is rarely in place, to enable the true delivery of cybersecurity solutions on a global scale.
This lack of results can drive middle-management frustration and budgetary tensions around cybersecurity internally, which in turn brews demotivation and further talent alienation away from cybersecurity functions. It is often also the lack of results (or insufficient or slow progress), which attracts the attention of auditors and regulators on these matters; those are often ‘low hanging fruits’ in absence of any strategic vision around cybersecurity.
This, in turn, is effective at drawing the attention of Executive Management towards the topic – but for all the wrong reasons. And when coupled with the increasing media and political attention around cybersecurity, it simply aggravates the tactical dynamics around cybersecurity. Driven by endemic fears of negligence claims and short-termism compliance obsessions, money – which wasn’t there yesterday – suddenly appears out of nowhere just to fix audit or compliance issues. Senior Executives can go to the media or claim with their peers that “cyber is on our agenda and money is there”, but in practice, the lines haven’t really moved at all – and the same old mistakes and habits are being perpetuated.
Over time, cybersecurity becomes an overhead and a problem – instead of a necessary barrier against real and active threats to the business. And, in practice, money is often simply wasted to put ticks in boxes. A large number of technology companies make a good living in that compliance space, but this eco-system is inherently unhealthy. This results in stagnating protection levels and low cybersecurity maturity, which is what the World Economic Forum report highlighted last year.
Large organisations, which find themselves in such a situation – and want to break these dynamics of failure – must rethink their approach and rewire their cybersecurity practice by acting at three levels.
- The profile of the CISO needs to be right in order to drive change. Look without complacency at the cybersecurity history across the firm, and at the barriers that have prevented progress. The CISO needs to have the right amount of business and management experience, personal gravitas and political acumen to be credible with all stakeholders across corporate silos (not just technologists) – these are attributes of seniority. Cybersecurity is not just a technical discipline.Cybersecurity is all about protecting information, which is at the heart of the organisation value chain and business processes. Therefore, only with the right attitude and experience will the CISO be able to reach out of IT to all stakeholders and drive success. Of course, the reporting line of the CISO is of paramount importance in that context. It should be to the CIO or the COO in most cases and delegating down must be avoided at all costs – as it would simply confuse objectives and create opportunities for political tensions with stakeholders. This would destroy any credibility around the real desire of Executive Management to drive change.
Raising the profile of the CISO (and their reporting line where necessary) will break the dynamics of talent alienation around cybersecurity. Sound governance, coupled with a better management and political acumen at senior level within cybersecurity, will break the dynamics of failure around delivery. Pinning success against a long-term backdrop and ensuring that the CISO and key personnel remain in place throughout will help Executive Management develop a true sense of purpose around cybersecurity, beyond short-termism or audit and compliance obsessions.
- The CISO needs to structure their relationship with all stakeholders as part of a strong Cybersecurity Governance Framework, positioning roles, responsibilities and accountabilities across the cybersecurity space and across the whole organisation from the top down.The CISO must also define a proper Target Operating Model for the cybersecurity team itself – which would give it a strong backbone, a clear structure and an unambiguous sense of purpose internally.
All of this is key to driving success. For example, you cannot imagine delivering a successful Identity & Access Management programme of work without the involvement of HR – and the business units if they are allowed to hire & fire directly. There needs to be clear demarcation lines around what gets done within the cybersecurity team and what remains outside of it.
The whole governance model should also address, without complacency, the full geographical spectrum of the business – and its true nature in terms of dependencies on third parties.
- The cybersecurity department should be seen as a true Business Unit, and therefore, every CISO should establish a long-term, clear and shared strategic roadmap – and be prepared to stay in charge for the time it will take to deliver it.Real and long-lasting change in the cybersecurity space will involve a cultural shift for most large organisations – and the embedding of a structured practice and a controls mindset in the way the organisation works. It will not happen quickly. It could typically involve an initial transformation cycle of several years, followed by a consolidation cycle of several years.
The CISO and key team members may have to consider their tenure over a 5 to 7 year horizon to genuinely drive change through. During the period, all actions (technical or not) must be pinned against a consistent long-term backdrop – including any unavoidable short-term tactical initiatives (typically driven by incidents, audit observations or compliance requirements). Inconsistencies and a constant reshuffling of priorities would simply kill the change momentum, as would the untimely removal of key personnel.
The resulting outcome should be a cyber resilient organisation, where cybersecurity is embedded in the business environment.
A long-term strategic roadmap for cybersecurity that is regularly updated, tailored to the business’s environment and provides financial perspectives – will bring multiple benefits:
- Traceability up to the organisation strategy and business lines’ requirements
- Improved overall resilience of business lines and cyber infrastructures
- Improved visibility and control over costs (where that’s a concern)
This should bring more attention from the Board and the business lines, and improve their engagement with the cybersecurity concepts – leading to more constructive discussions around cybersecurity budgets and costs.
Over time, focus on information risk should drive meaningful intelligent actions, and cybersecurity should become a valuable business function at the heart of the organisation – not just an IT department that deals with audit and compliance issues.
This article is based on an earlier article by Corix Partners, which Corix Partners (JC Gaillard) and Business Digital Security (François Gratiolet) have revisited jointly to reformulate its content as the foundations of a road to cyber resilience.
Find out more about how your business can truly protect its future from cyber threats by contacting Corix Partners. Corix Partners is a Boutique Management Consultancy Firm, focused on assisting CIOs and other C-level executives in resolving Security Strategy, Organisation & Governance challenges.