In earlier articles this year, we examined the challenges the CIO faces around Information Security, the importance of the CISO’s reporting line, and the fundamental role the Board of Directors has to play to drive security transformation.
In part 2 of this short series, we revisit and further develop some of these aspects in line with new reflections, as well as addressing feedback we have received on past articles. Click here to read part 1.
Part 2 – New Directions
A structured InfoSec practice can be a key ally for the CIO, but the Board must reward protection to attract and retain talent
Organising Information Security for a changing IT world
In such context, a strong Information Security practice can be a key asset for the CIO. However, a strong practice must have a clear sense of purpose and a visible backbone upon which the CIO can rely to keep a grip on a changing IT world.
In practice, the CIO must not allow separation to be blurred between first and second lines, and should structure the organisation accordingly.
Enforcing a degree of separation between risk management and controls enforcement within the CIO’s organisation could lead to the emergence of 3 distinct functional activities:
- An “Information Risk Management” function, aggregating all traditional second line activities across that space
- An “IT Security” function, focused on the architecture of functional and technical controls (essentially designing IT Security measures and working with all IT stakeholders in that respect, both internally and externally)
- A “Security Operations” function, focused on driving the implementation of controls through the application of technical standards and procedures (these should be designed jointly with the “IT Security” function, based on policies set out by the “Information Risk Management” function and under their validation). The “Security Operations” function (externalised or not) could take a direct role in the delivery of some of these – in particular in the Security Monitoring or Identity Management spaces – and should deal with associated events and incidents
The “Information Risk Management” function should report to the CIO and interface with all non-IT stakeholders, internally and externally, as necessary (Risk, Compliance, internal and external Audit, regulators etc). The other two functions could be structured at a CIO-1 level (possibly under the CTO or the Head of IT Infrastructure, where such roles exist) and would interface with all IT stakeholders as required.
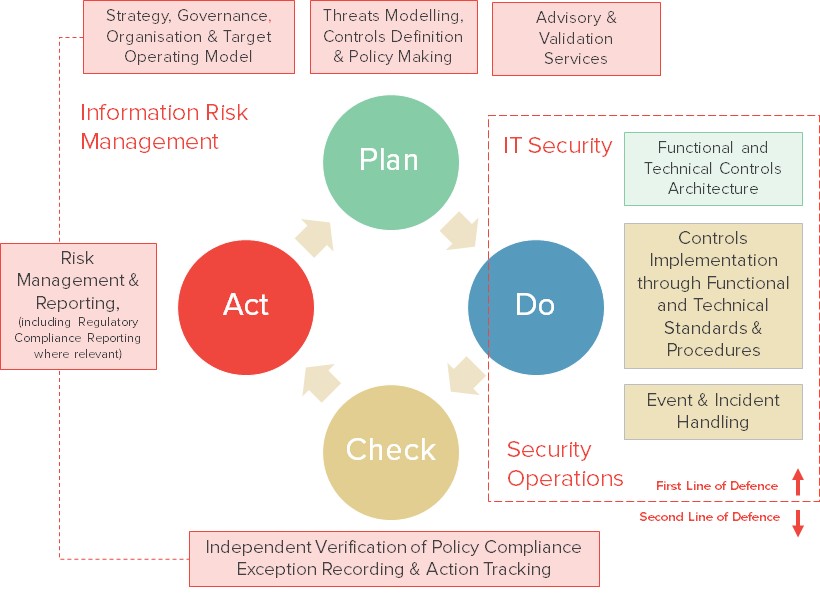
What happens to the CISO tag in such context? It continues to imply a degree of seniority in the role and, if kept in this type of model, should be applied to the “Information Risk Management” function – which is the most complex from a corporate perspective, and has the broader managerial remit.
This is leading us to suggest an alternative organisational model for large corporates to structure InfoSec in the portfolio of the CIO – updating the previous model published in April 2015 (itself the result of earlier research work, going back to 2012).
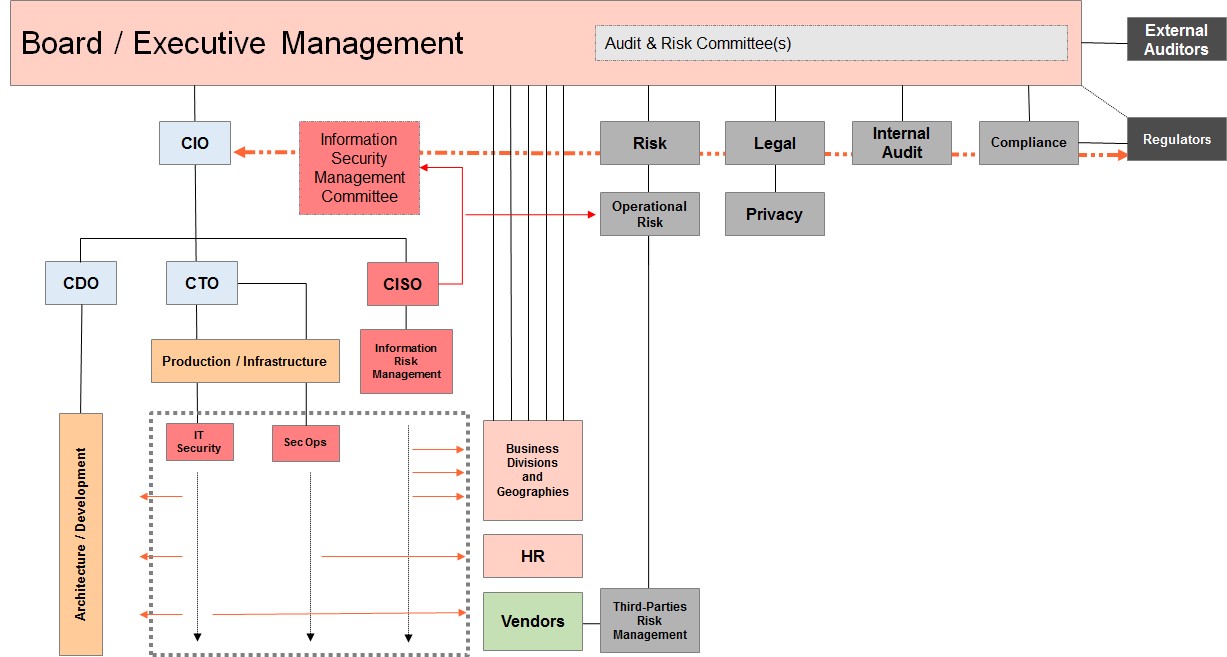
Moving towards the type of model highlighted here could imply splitting legacy CISO roles, and developing a different and more structured target operating model around Information Security.
It would, invariably, involve some form of redistribution of personnel, and skill sets may have to be reviewed and adjusted. In some cases, it may highlight a critical need to invest more in resources to cover areas where little had been done up to now.
The CIO and the Board should consider this a major step towards building a resilient IT practice in the face of virulent cyber threats – rather than continuing to pour resources, on an ad-hoc basis, into arbitrary technical projects.
The argument that this type of model could lead to a “conflict of interests” for the CIO needs to be handled with common sense (in particular in large organisations) and it is key to look beyond simplistic positions. A sound and comprehensive operating model is key to driving change, if that’s what is required around Information Security. Arbitrary separations often fuel internal politics and can create unnecessary conflicts.
Boards must incentivise CIOs on cyber security
In past articles, we have queried the control-mindedness of CIOs and implied that it was a major prerequisite for the Board to consider placing Information Security in the CIO’s portfolio.
The events of the past few years and the emergence of unprecedented media and political interest around cyber security, as a result of major cyber breaches, make it hard to imagine that any CIO in any large organisation would not take such threats seriously.
Beyond the control-mindedness of the CIO, what matters most today is the way the CIO addresses cyber security priorities – and this is something on which the Board can have a direct influence.
The Board should take an active interest in cyber security matters and drive real action in that space, but it can only work in real life if it translates into real incentives for real people.
CIOs have always been incentivised on cost control and the timely delivery of functionality. It is time for the Board to incentivise CIOs also on the delivery of security controls and the actual protection of the organisation from cyber threats.
These incentives should cascade down to attract and retain talent. Only attracting talent, retaining it over the right timeframes, and applying it at the right level across a structured InfoSec organisation will drive more comprehensive and structured protective operating models – and disrupt the mediocrity dynamics around Information Security, to create the conditions of a true security transformation.
Managing Director
Corix Partners
Contact Corix Partners to find out more about developing a successful Information Security Practice for your business. Corix Partners is a Boutique Management Consultancy Firm, focused on assisting CIOs and COOs in resolving Security Strategy, Organisation & Governance challenges.

